Keys, Accounts, and Seeds: How Web3 Wallets Work
Un-ironically Putting the Crypto in Cryptography
It’s easy to take wallets for granted without thinking about the mechanisms underneath that enable self-custody over our assets. Wallets use layers of cryptography to keep assets secure, and each level from seed to account does something fascinating.
Today’s write-up explains how blockchain accounts work and what really goes into creating a new wallet. Enjoy.
Sections
What are Wallets?
Where do Seed Phrases Come From?
How are Private Keys Created?
How are Public keys Generated?
How are Account Addresses Generated?
Are There Practical Benefits From Understanding Wallets?
In Conclusion
*Thank you to Ziad for proofreading.
First, Wallets
Wallets are simply ways to access accounts on blockchain networks. Accounts have addresses that funds can be sent to, public keys that prove who they are, and private keys that authorize transactions. Even more private than private keys though, are the seed phrases that create them.

Where Seed Phrases Come From
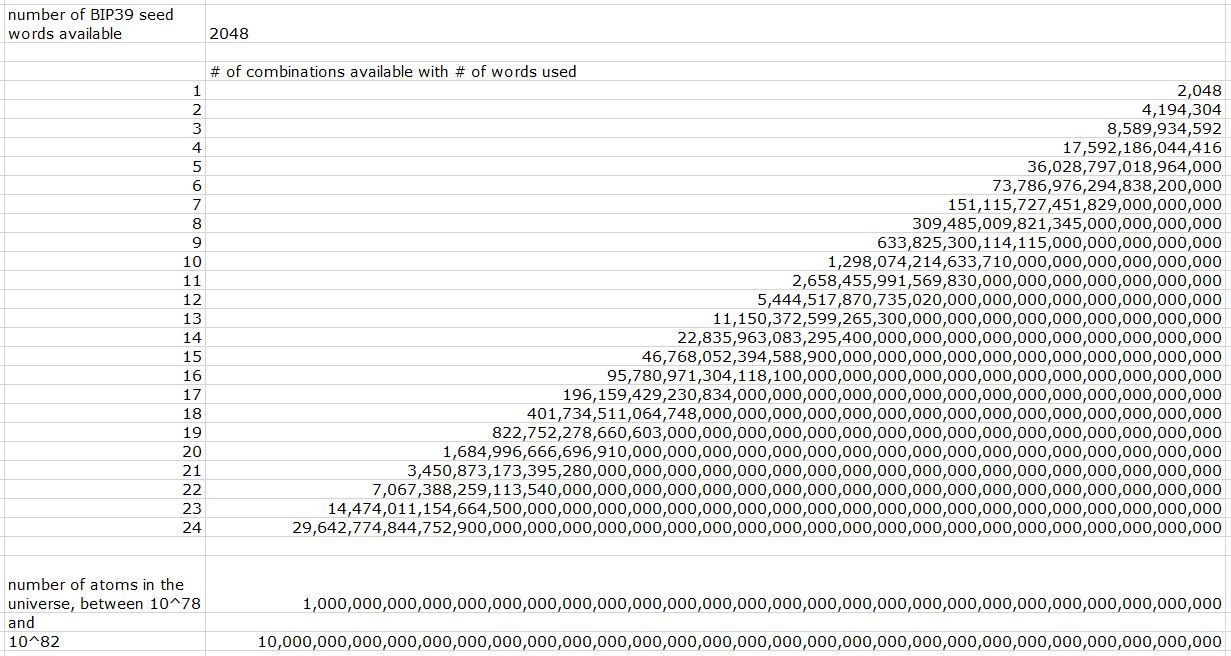
The way seed phrases are generated across many blockchains follows the Bitcoin model, introduced in BIP-32 and BIP-39. Listed within are the 2048 words that form all possible combinations of seed phrases. The words themselves aren’t strictly necessary, but help us note the keys to our assets as words instead of very large numbers.
A seed phrase can be represented as 12 words, but that’s not how they start. Instead, they’re created as a series of 128 bits (ones and zeros) generated at random, plus 4 extra ones. These 132 bits divide into 12 words. In essence, each word is just a way to represent 11 ones and zeros. The BIP-39 proposal defines which sequences of bits correspond to which of the 2048 words.

The randomness of the bits that make up the seed is essential to the security of its accounts. Approaches to this “entropy generation,” or randomness, can vary from one wallet provider to another. Once a seed is created though, it goes through some additional cryptographic steps to keep itself secret.
How Private Keys Are Created
While you only need one seed phrase, you can have many private keys linked to one. Seed phrases give access to all the private keys that they create, whereas private keys only give access to specific accounts. A seed phrase is like a master key that can unlock every deposit box at your personal bank, whereas private keys only unlock one box (i.e. account) each.
Seed phrases create private keys by going through a couple of cryptographic steps. First, our seed phrases are added with some extra random data, called a salt, and passed through a hash function to create a “root key.” Hash functions take any data and represent it in a specific format, in this case 512 bits.
Read more about hash functions in my previous write-up on Merkle Trees.
Our 512 bit root key is then hashed again with a different function. The result is a sequence of another 512 bits that we split down the middle to create two things: the sequence on the left becomes the “master private key,” and the right sequence becomes “chain code.” The master private key can access all accounts that come from the same seed phrase, whereas the chain code serves as additional randomness that is used when new accounts are generated.
Finally, to create a private key that actually belongs to a new account (and not the seed phrase itself), we count up from 0. The first account a wallet creates will have an index number of 0, the next will have 1, and so on. We’ve gone through no less than three functions to create private keys, each serving an essential purpose for security.
How Public Keys are Generated
Public keys are generated with a method known as “elliptic curve cryptography.” This method uses an elliptic curve like the one below with a specific shape and starting point that varies from one blockchain to another. To generate a public key, a private key is represented as a number and multiplied by the starting point for that elliptic curve (and by extension, blockchain).

By virtue of mathematics, the resulting number is also a point on the elliptic curve. That number represents the public key. It’s practically impossible, however, to divide it to find out which starting point was used to get there. When compared to a classic form of encryption known as RSA, a study titled Universal Security noted that “breaking a 228-bit RSA key requires less energy than it takes to boil a teaspoon of water. Comparatively, breaking a 228-bit elliptic curve key requires enough energy to boil all the water on earth.”
How Wallet Addresses are Generated
One more level of abstraction is required to go from public keys to account addresses. While blockchains could have used public keys as the addresses themselves that people share, there’s a significant security reason why the distinction today exists. An address is essentially the public key after it’s gone through some hash functions.
The hash functions hide the public key so that an account can receive funds using the address only. As long as it never broadcasts a transaction, it’s public key remains hidden. This protects the account against potential future ways to break encryption that could allow a private key to be derived from a known public key. As a result, rotating funds to accounts that remain dormant is a prudent, long-term security measure.
Wallets, Practically
When you create a new wallet, all the steps above provide you with a seed phrase and an account. As mentioned, there can be many accounts created from a single seed phrase, each with its own private key for authorizing transactions. If that account’s private key is compromised, it does not place at risk the other accounts from that seed phrase. That said, it can be very difficult to determine if a private key or a seed phrase was compromised.
Once new accounts are created, they can be added to other wallets that have entirely different seed phrases. This is because the seed phrase is only used in the generation of the account and its private key; not in the ongoing verification of transactions. That’s what the private key is for. As a result, anyone can take private keys from any wallet they’ve created, and import them all into a single interface.
If the single interface used to access accounts is a hot wallet (entirely a bit of software on a personal device), there are significant security risks. Private keys authorize transactions, and must be stored somewhere to provide that authorization when needed. Hot wallets store private keys on devices or in the cloud, making them very easily accessible by hackers. Cold wallets instead store private keys on devices that don’t connect to the internet, protecting them from prying eyes.
In Conclusion
Blockchain accounts make security deceptively simple. The difficulty required to compromise an account makes such attacks infeasible, allowing full financial self-custody ion ways that haven’t been possible before. While blockchains may be slow today, they were designed from the beginning to scale.
With security being a dependency we can lean on blockchain for, and people creating disposable wallets for even added security, are there enough wallets to go around? Even with only 2048 words, there are more possible accounts than there are atoms in the universe.
Thank You & Additional Reading!
Thanks a lot for reading! Here are some more resources if you'd like to dive deeper.
Subscribe below if you haven’t for more simple write-ups on blockchain concepts!
If you’ve signed up, thank you! Consider sharing this write-up with others below.
Share a Summary
Thanks again, please consider sharing this write-up using the button below!
Stay kind. Stay curious.



